Identity and Access Management
Add deep context, intelligence and security to decisions about which users should have access to your organization’s data and applications, on-premises or in the cloud
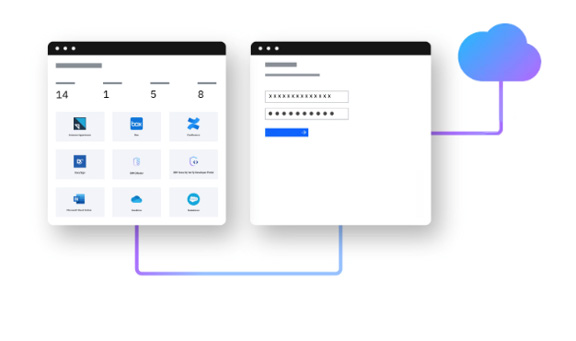
Transform IAM with hybrid cloud
Modernized, modular IBM Security™ Verify solution provides deep, AI-powered context for both consumer and workforce identity and access management. Protect your users and apps, inside and outside the enterprise, with a low-friction, cloud-native, software-as-a-service (SaaS) approach that leverages the cloud. For legacy, on-prem apps, the Verify Access version provides a smooth path to cloud, so you can transition at your own pace.
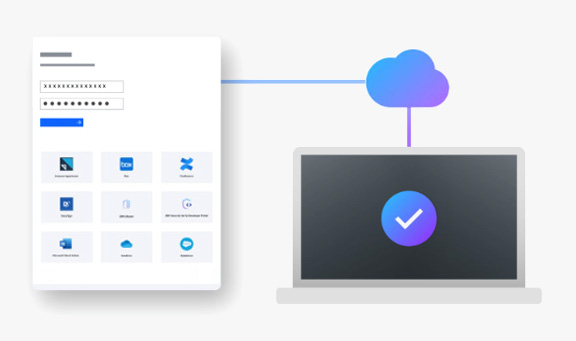
Core Verify features
Built-in innovation to create secure, low-friction access for your customers, employees, contractors and partners..

Single sign-on
Centralize access control for cloud and on-prem applications. Reduce password fatigue.
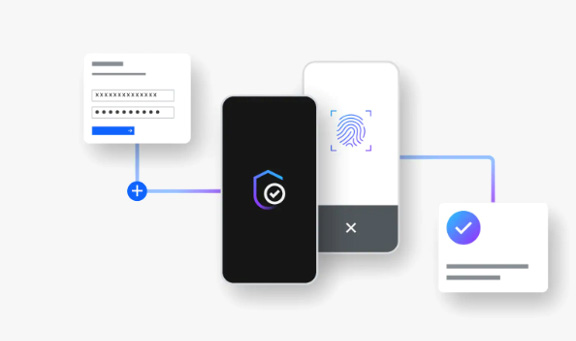
Advanced authentication including passwordless
Add a security layer such as MFA or go fully passwordless for faster access to data and applications.
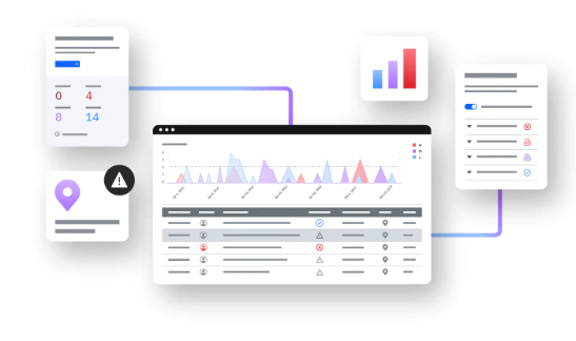
Adaptive access
Continuously evaluate user risk by applying machine learning for higher accuracy.
Consent management
Add a security layer such as MFA or go fully passwordless for faster access to data and applications.
Use templates for detailed requirements to help address privacy laws and self-services.
Explore Consent Management.
Explore Consent Management
Lifecycle management
Connect application access with business governance workflows.
Explore Consent Management
Identity analytics
Scan for risks across users, entitlements and applications.
Explore Consent Management
Simplifying secure identity and access for over 27 million users.
The IBM Office of the CIO case study
Download the CIAM's Buyers Guide